Privileged Container with sensitive mount
In this lab you will be creating a container with privileged Security Context, with root level access in the default Namespace of your EKS Cluster. This privileged container will also have a sensitive directory from the host, mounted and accessible as a volume within your container.
This exercise will generate two different findings, PrivilegeEscalation:Kubernetes/PrivilegedContainer which indicates that a container was launched with Privileged permissions, and Persistence:Kubernetes/ContainerWithSensitiveMount indicating a sensitive external host path mounted inside the container.
To simulate the finding you'll be using a pre-configure manifest with some specific parameters already set, SecurityContext: privileged: true and also the volume and volumeMount options, mapping the /etc host directory to /host-etc Pod volume mount.
apiVersion: v1
kind: Pod
metadata:
name: ubuntu-privileged
spec:
containers:
- name: ubuntu-privileged
image: ubuntu
ports:
- containerPort: 22
securityContext:
privileged: true
volumeMounts:
- mountPath: /host-etc
name: host-etc
volumes:
- name: host-etc
hostPath:
path: /etc
restartPolicy: Never
Apply the manifest shown above with the following command:
This Pod will just run once, until it reaches the State Completed
Within a few minutes we'll see the two finding PrivilegeEscalation:Kubernetes/PrivilegedContainer and Persistence:Kubernetes/ContainerWithSensitiveMount in the GuardDuty Findings console.
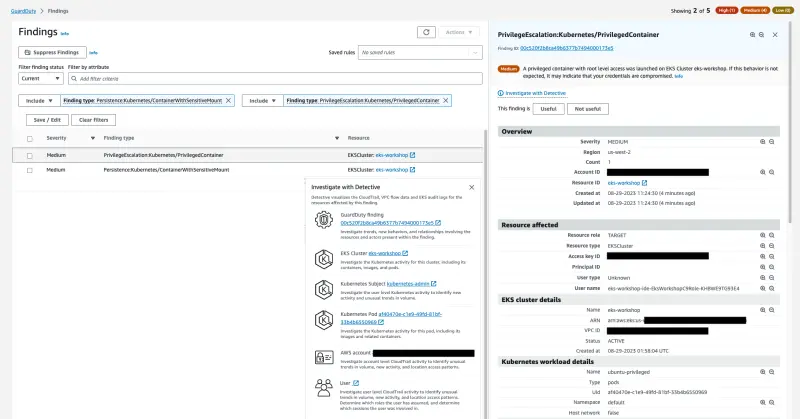
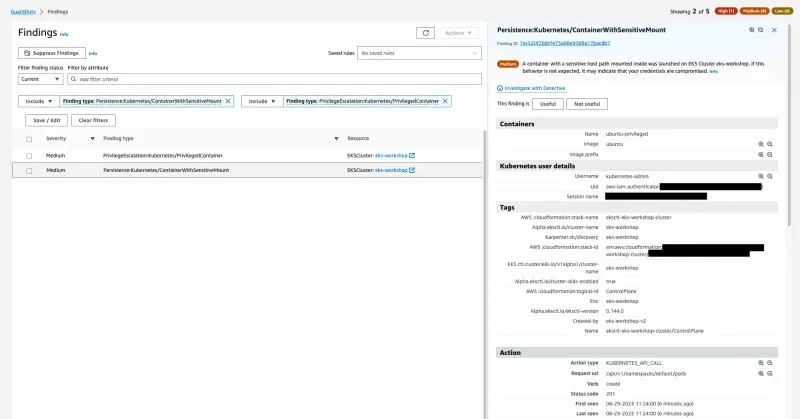
Once again take sometime to analyze the Finding details, Action, and Detective Investigation.
Cleanup the Pod by running the command below: